AWS IAM to Authenticate Against RDS Instances & Aurora Clusters
Author: Shailesh Rangani | 4 min read | February 26, 2020
You can use IAM DB authentication to authenticate your RDS instance or Aurora cluster without a password. It uses an AWS-generated token for authentication. It works for PostgreSQL and MySQL databases on RDS.
In the traditional method, if you want your application to talk to the database, you need a password. For many organizations, there is a JSOX requirement for rotating passwords periodically, but this task can be tedious since you’ll need to update your application configuration and test the application every time.
What if there is a feature that generates a random password, authenticates to the database and this password is only valid for a few minutes? That can be achieved against amazon RDS and Aurora clusters using IAM options!
These IAM tokens are generated and managed by AWS and they have a lifespan of 15 minutes, hence not needing to worry about password resets to meet your auditing requirement. Even if this not an auditing requirement, this can help you in avoiding unnecessary logins to the production database. IAM authenticate database via SSL so all data transmitted from application to the database are encrypted.
Let’s dig into the authentication to PostgreSQL RDS using AWS IAM.
Below are high-level steps on implementation:
1. Enable IAM authentication at RDS level
Use below “aws cli” option or AWS console to enable IAM authentication for a given instance. If you are running on the Aurora cluster, enabling this option at the cluster level will automatically apply this configuration to all its instances.
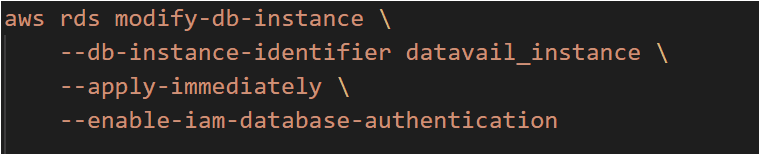
where datavail_instance can be an Aurora cluster or an RDS instance.
2. Create IAM policy
The below example policy allows an IAM user to connect to a DB instance using IAM database authentication.
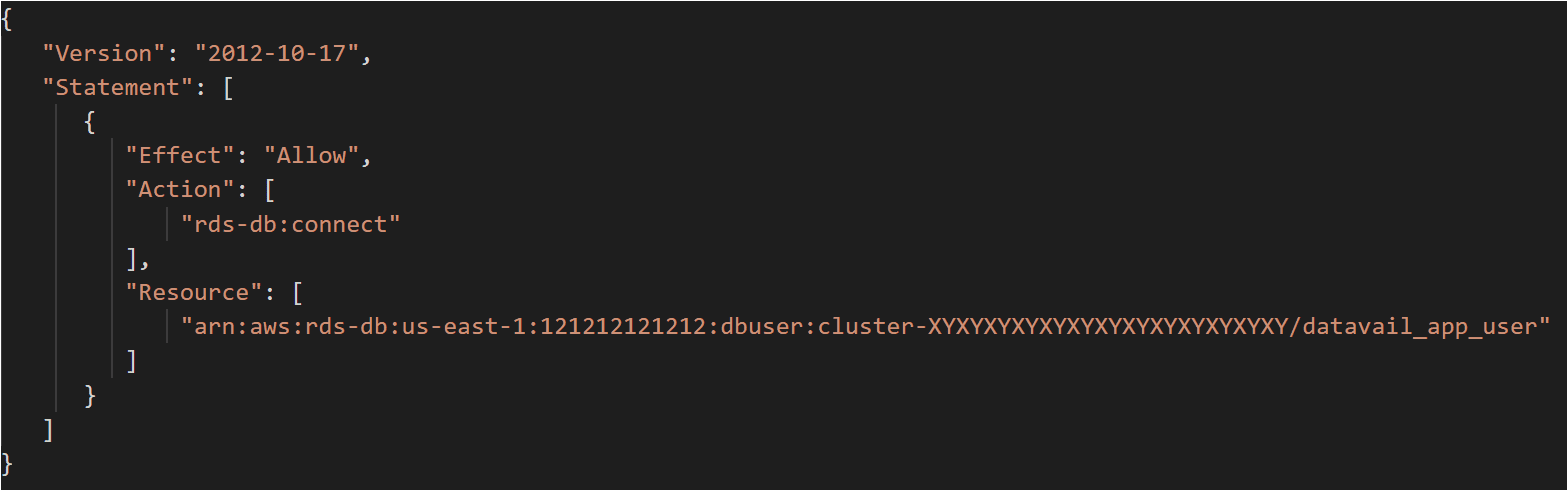
121212121212: is AWS account number.
XYXYXYXYXYXYXYXYXYXYXYXYXY: is the database resource ID (in case of RDS) or cluster resource ID (in case of Aurora).
datavail_app_user: is database username for which you want IAM auth to be enabled.
3. Attached policy to AIM user or AWS resources
Create IAM policy and attached to AWS resources where your application is hosted (i.e. EC2 instance, ECS, etc.). You can also attach this policy to the respective IAM user, in this case, you will have to use access key ID and secret key on EC2 instance where your application is running.
4. Create a database user
Now create a database-level user (let’s say datavail_app_user), you do not need to provide a password for this user while creating this.
Below is an example of PostgreSQL. Refer to this link for MySQL options.
PostgreSQL:
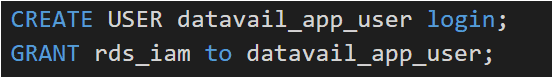
5. Client-side certificate configuration
Download the client-side certificate bundle file here. If you are using a 2015-root certificate, it expires in 2020, refer my previous blog to rotate them to the 2019 version.
6. Manual Validation
Before jumping to connectivity from application to database, it’s advisable to validate that the token is generated successfully, and connectivity works as expected. Just as side note, if you see the token generated by policy granted to IAM user vs policy granted to AWS resources (i.e. EC2, ECS, etc.), you will find the difference in token length. The token generated via assumed role is bigger in length.
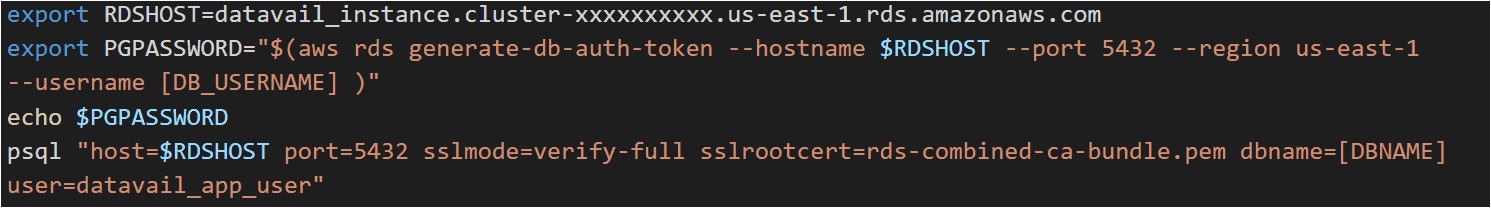
This should get you in the database. As mentioned, this token is valid for 15 minutes and expires automatically after that.
7. Sample Application code
The below is a sample working application code from Python and Go to validate IAM authentication against RDS/Aurora for your reference.
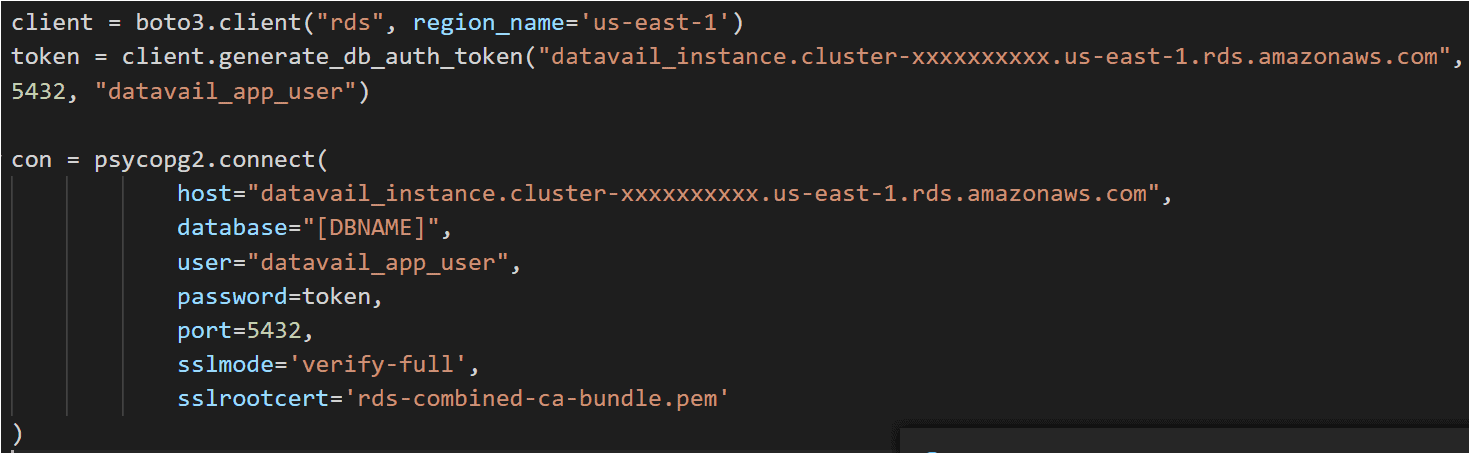
Python:
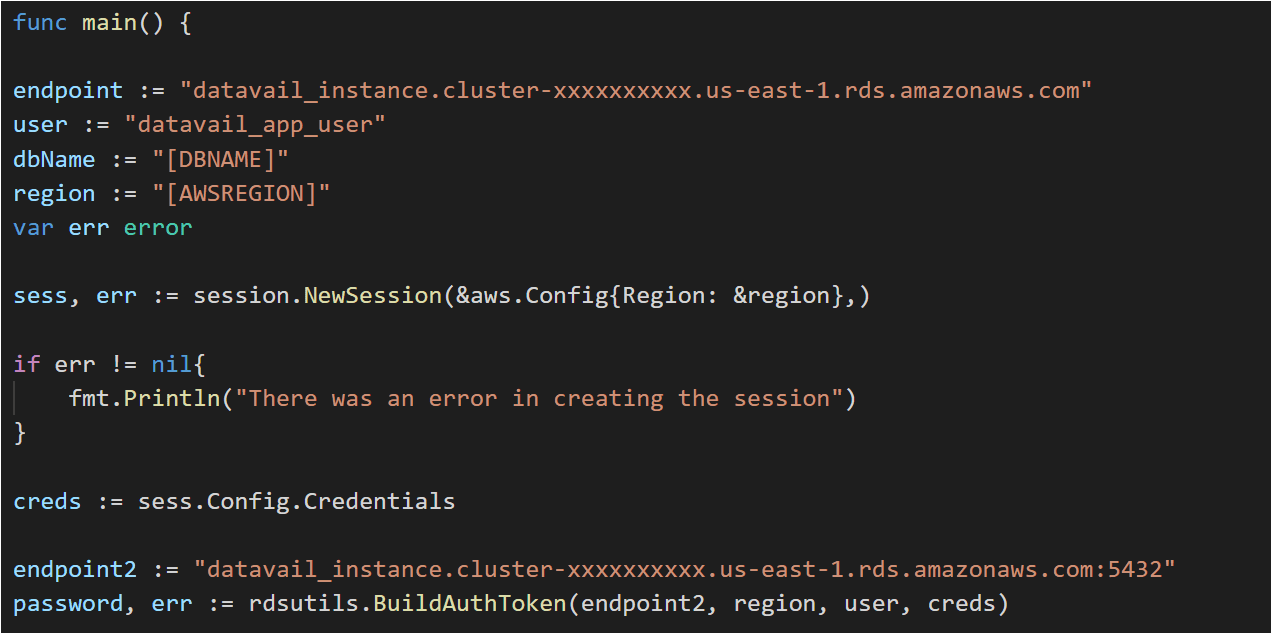
Go Lang:
Recommendation
IAM authentication should be used for that application workload:
1. Which can be easily re-triable
2. For which number of connections required are less than 256 per second
Final Thoughts
IAM authentication comes with numerous benefits like in-transit application encrypted traffic to RDS, auditing requirement of password rotations, centrally managing database access for all individual databases, instead of managing them individually; and using IAM profile credential of that EC2 instance (if the application is hosted on EC2 instance) to generate token and connect instead of using password. Datavail is a Certified AWS Partner that can help you analyze and transition your application workload to use IAM authentication for RDS. Contact us to learn more.
